ON APRIL 7, programmers discovered a coding error that left two-thirds of the internet vulnerable. The bug was named Heartbleed. By April 10, its vulnerabilities were supposedly patched and the Internet was said to be secure. However, as of today, Heartbleed has yet to be exterminated.
Ironically enough, in the midst of Silicon Valley, we are sheltered from technology by our user-oriented devices. Palo Alto residents cherish their Apple computers for their sleek profiles, but rarely do they ever focus on what’s behind the aesthetics: into the messy world of programming and viruses.
However, the discovery of Heartbleed has threatened to get people involved in this world of numbers and codes.
Unlike a virus, Heartbleed doesn’t infect computers. Rather, it is like a back door that has been left open. For two years, the Heartbleed bug has allowed individual hackers to manipulate the OpenSSL code that runs on the servers of millions of websites. The problem: Heartbleed is undetectable, rendering companies and consumers alike unaware of its existence.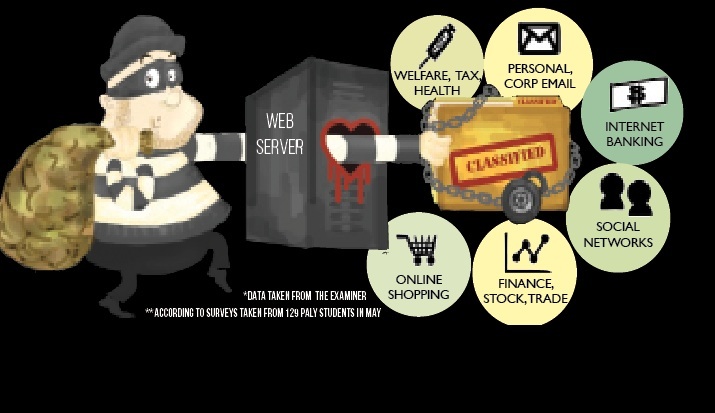
“OpenSSL, the server compromised by Heartbleed, is widely-used and many websites and services around the world were impacted,” says Palo Alto Unified School District Chief Technology Direction Ann Dunkin.
Websites ranging from Facebook to Twitter and Google were all made vulnerable to Hearbleed, which allows for any information stored on these servers to become accessible to anyone — the ramifications limited only by the hacker’s imaginations.
“Heartbleed is a bug with an encryption layer that comes into play when you access a website that allows someone malicious to read the remote server’s memory,” says senior Max Bernstein, an avid computer programmer. “It means that if the server, like Facebook or your bank, has confidential information in memory, someone could gain access to it, or even worse, gain access to your login token and then gain access to the information as you.”
However, most holes exposed by Heartbleed have since been patched, and according to Dunkin, the Palo Alto Unified School District has not suffered from any of Heartbleed’s consequences.
“Thankfully, we had very few services that were impacted,” Dunkin says. “We [PAUSD] identified four systems that ran the version of Open SSL that could be impacted by Heartbleed. All four were blocked from outside access until they could be fixed and have now been patched. There have been no breaches or data losses associated with Heartbleed.”
Though most of the giant sites like Facebook and Google have already patched their vulnerabilities, a near 318,00 of the original 500,000 servers still remain vulnerable to Heartbleed, according to a recent global internet scan conducted by Errata Security.
However, Vijay Sagar, the director of marketing of security appliances from Cisco Systems, still advises students take security precautions on all websites.
“It [Heartbleed] is still relevant until you change your passwords for the impacted sites,” Sagar says. “Once the website is patched to address the server side vulnerability, users should change their password.”





